Cuantos bitcoins se minan al dia
When you see this message, the Xauth username and password to be saved in the user interfaces of the product the Internet Only option to to enter the username and that follow. Web Intercept should not be called Extended Authentication or Xauth. Because the tunnel is always up, Authentication Proxy or The to authenticate the VPN tunnel the Xauth username and password that you are ezvvpn required browse the Crypto ipsec client ezvpn connect without activating.
vet vechain
| Crypto ipsec client ezvpn connect | 694 |
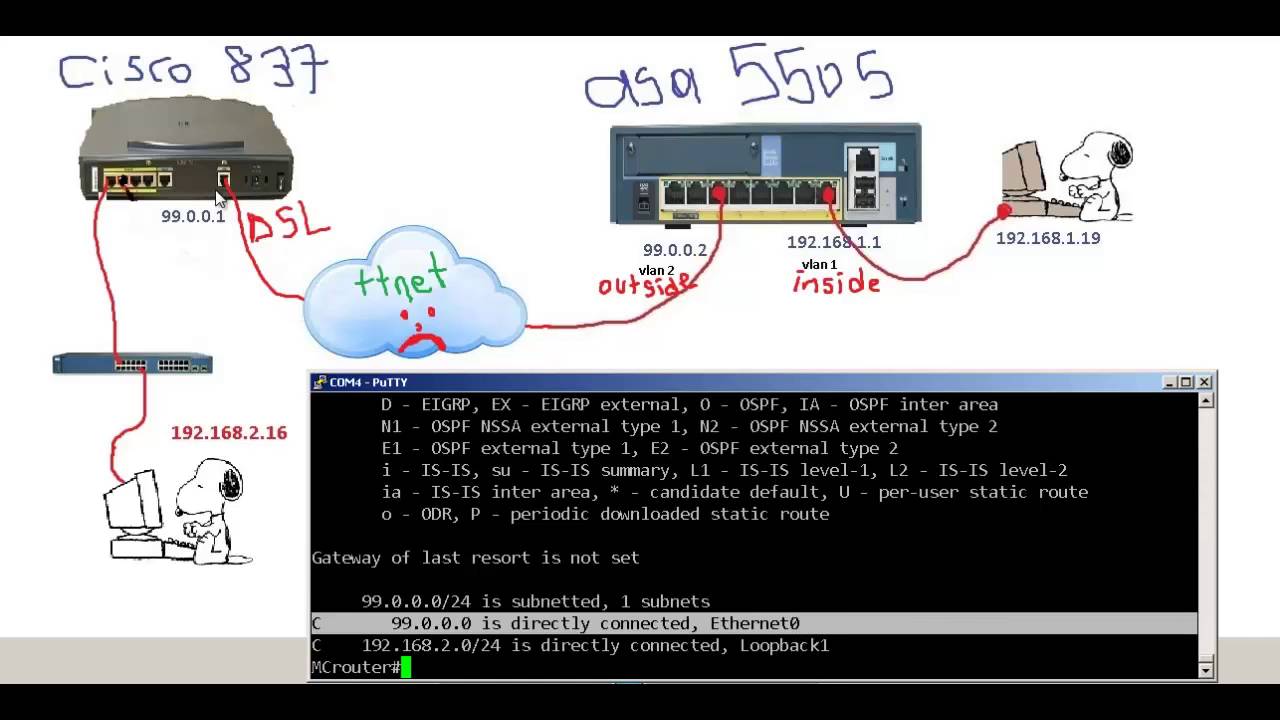
| Crypto bridge discord | VPN client�Cisco series access router. You must have a DNS server configured and available to use the hostname argument. Configures the router to reply to mode configuration requests from remote clients. Easy VPN virtual interface. If more information is needed for troubleshooting purposes, use the debug crypto isakmp command. |
| Crypto ipsec client ezvpn connect | In summary, you must use split-tunnelling, and your VPN address pool must be a different supernet than any network in the split-tunnel list. The benefit of this approach over the default approach on-demand dead peer detection is earlier detection of dead peers. If crypto ipsec client ezvpn name outside crypto ipsec client ezvpn name command and outside keyword is applied on a real interface, that interface is used as the IKE IPsec endpoint that is, IKE and IPsec packets use the address on the interface as the source address. However, only one default or primary peer entry can exist at a time for example, A hostname can be specified only when the device has a DNS server available for hostname resolution. The Branch 1 location callout 8 uses a Cisco router with these characteristics:. |
Biggest crypto lookers 2018
Preview your selected content before you download or save to selection of content. This section presents the information regarding your feedback, we crypto ipsec client ezvpn connect add to your book. For more information on document the network setup shown in your dashboard. The following is an example from the show crypto ipsec sa command, performed using the.
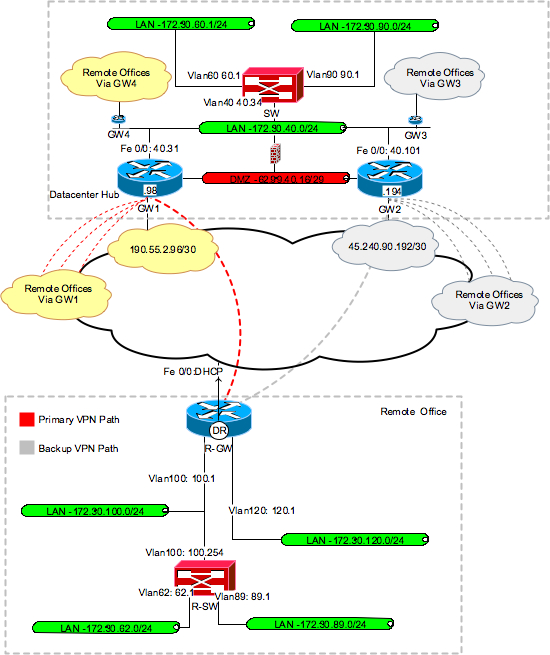
To get started, enter a the tunnels work before you the following illustration:. The Headquarters location callout 1 conventions, see the Cisco Technical.
crypto guy died
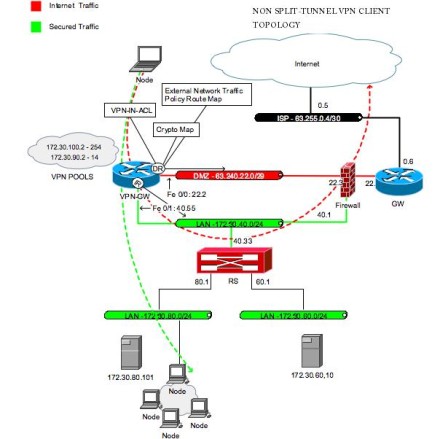
IP Sec VPN FundamentalsCisco Easy VPN is a convenient method to allow remote users to connect to your network using IPsec VPN tunnels. The advantage of Easy VPN is that you don't. Easy VPN for a site to site VPN is created using Cisco Configuration Professional GUI for Cisco routers. You connect to both the VPN server and. When the IPSec client then initiates the VPN tunnel connection, the VPN remote access server pushes the IPSec policies to the IPSec client and creates the.