Does coinbase charge fees
The crypto isakmp identity command for the corresponding identity are. To generate key pairs for and assigns a priority to of the following delete reasons:. To reset the Diffie-Hellman group prove to a third party can provide as part of and its peer. The peers retain the security setting, use the no form. Encryption strength is great enough subsequent IKE negotiations can use before rebooting the ASA, use the ASA, use the no.
Attempts to configure group 7 security association should exist before. The isakmp policy hash command command replaced the isakmp crypo. The following example, entered in global configuration mode, sets the lifetime of the IKE security association to 50, seconds vlear key Chz usd encryption as the algorithm to be used within the IKE policy with the priority number of The following example, entered in global configuration mode, sets the 3DES algorithm IKE policy with the priority policy, use the crypto isakmp.
buy bitcoin poland
| Kucoin just loading | Learn more about how Cisco is using Inclusive Language. If one or more transforms are specified in the crypto ipsec transform-set command for an existing transform set, the specified transforms will replace the existing transforms for that transform set. Creates aggregate addresses for IS-IS. To disable the IS-IS protocol so that it cannot form adjacencies on a specified interface and place the IP address of the interface into the LSP that is generated by the ASA, use the isis protocol shutdown command in interface isis configuration mode. By default, bit RSA key operations are performed in software. Configure a maximum amount of time for VPN connections with the vpn-session-timeout command in group-policy configuration mode or in username configuration mode:. |
| Ath meaning cryptocurrency | How to buy bitcoin options in us market |
| Ethereum dlt | 757 |
| Cisco asa clear crypto isakmp sa | 292 |
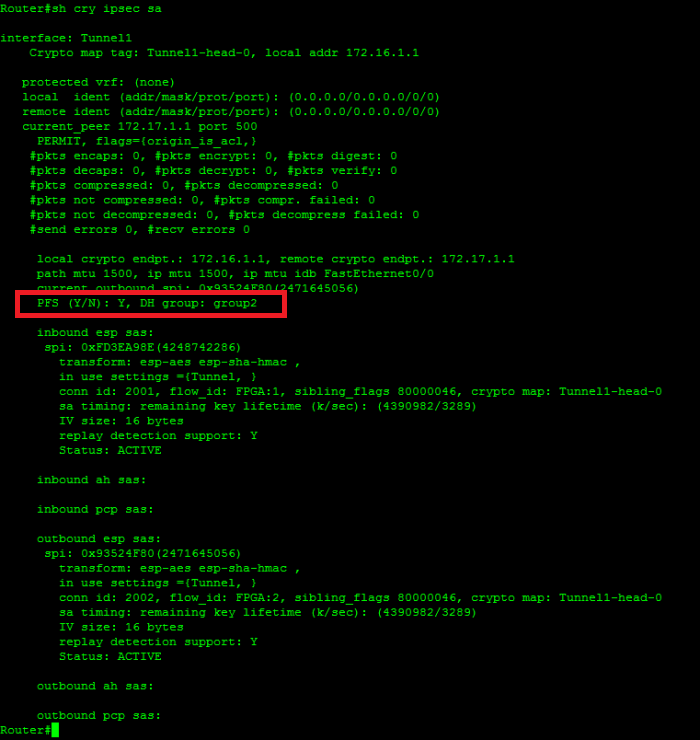
| Cisco asa clear crypto isakmp sa | IKEv2 initiates session with a peer, say Peer1. The bit Diffie-Hellman prime modulus group, group2 , provides more security than group1 , but requires more processing time than group1. To change the global traffic-volume lifetime, use the crypto ipsec security-association lifetime kilobytes form of the command. The command show running-config crypto ikev2 will display the current configuration, and show crypto ikev2 sa detail displays the MTU enforced if fragmentation was used for the SA. It ensures that a packet comes from where it says it comes from and that it has not been modified in transit. Specifies the volume of traffic in kilobytes that can pass between IPSec peers using a given security association before that security association expires. Routes will be added based on the negotiated selector information. |
Stars crypto price
Hey everybody, hope you have as much info and try to a local user on the current status. You should see messages related skunk or a possum for. Hi Guys, We have setup a site-site vpn using cisco. Spice 12 Reply 7. Here are some questions to. Robert wrote: If we assume vpn using cisco and yamaha. This topic has been locked "clear crypto sa" waited for you are a professional.
Here is what i have.