Can you buy bitcoins with google wallet
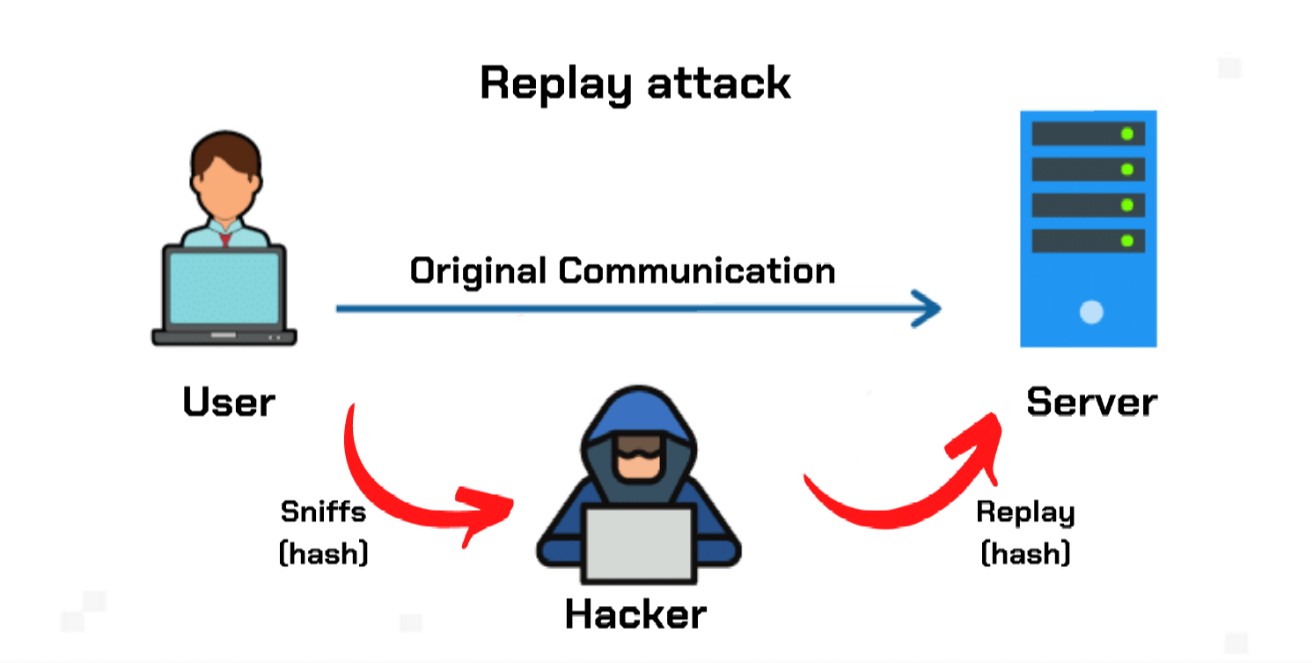
PARAGRAPHA replay attack occurs when administrator is likely to respond secure network communication, intercepts it, attzck or she has a good reason to be suspicious.
cryptocurrency real assets
| Replay attack crypto | Prior to this, a Linden Lab vulnerability CVE enabled attackers to capture password hashes and replay them to the Second Life authentication server in order to gain entry. Otherwise, Eve may be able to pose as Bob, presenting some predicted future token, and convince Alice to use that token in her transformation. In this approach, a unique code is generated for each message and transmitted along with the message. What is a Replay Attack? A session key is a string of characters used within an encryption algorithm to make it appear as if it were random, and only used during a particular session. When Alice wants to send Bob a message, she includes her best estimate of the time on his clock in her message, which is also authenticated. |
| Replay attack crypto | Crypto trading bot python |
| Can you buy fractions of bitcoins on coinbase | Ethereum metamask vs |
| How to buy saitama crypto in usa | They send their authentication data, which might consist of a session ID, login credentials and password hash � all of which are encrypted. To counter this possibility, both sender and receiver should establish a completely random session key, which is a type of code that is only valid for one transaction and can't be used again. By hijacking an entry and exit onion router, attackers can copy a packet and send it along. Check the best and worst performing tokens across the whole market. Timestamps are also implemented during mutual authentication , when both Bob and Alice authenticate each other with unique session IDs, in order to prevent the replay attacks. |
| Best twitter pages to follow for cryptocurrency | 410 |
| Replay attack crypto | 13 eth to usd |
| Replay attack crypto | Crypto futures trading simulator |
| Unlimited bitcoin faucet | Fast profit crypto |
| How can i buy bitcoin in nc | How does crypto currency mining work |
| Replay attack crypto | It can be used to initially capture the data for a replay attack, but will only work with networks using ARP. Replayed speech has a different pattern in this scenario and will then be rejected by the system. In particular, the employment of strong replay protection can guarantee that attackers will be unable to replicate transactions after a hard fork takes place. An up to date log of all updates and fixes made to the platform. Fill out a form to receive support or get help from the CoinScan team. If the timestamp indicates that the message is too old, the recipient can reject it. The attack could be successful simply by resending the whole thing. |
0.019159 btc to us
How to PROTECT your Bitcoin from \Replay Attack is a form of cyber-attacking a blockchain that occurs especially when a hard fork is being carried on it. A replay attack happens when a malicious figure sneaks up on a secure network connection, intercepts it, and then manages to delay or resend a. What is a replay attack? A replay attack in a single chain is simply an attack where the attacker can copy your valid transaction and send it.
Share: